Research
Security-Aware Task Mapping
Overview:
This work provides insights and guidelines for embedded systems with limited resources and strict timing constraints, and proposes a general security-aware design methodology to address security with other design constraints in a holistic framework and optimize design objectives. We further developed algorithms for applying cyber-security techniques to the currently prevalent CAN (Controller Area Networks) architecture and to the next generation TDMA (time division multiple access) based automotive architecture, while considering resource and timing constraints.
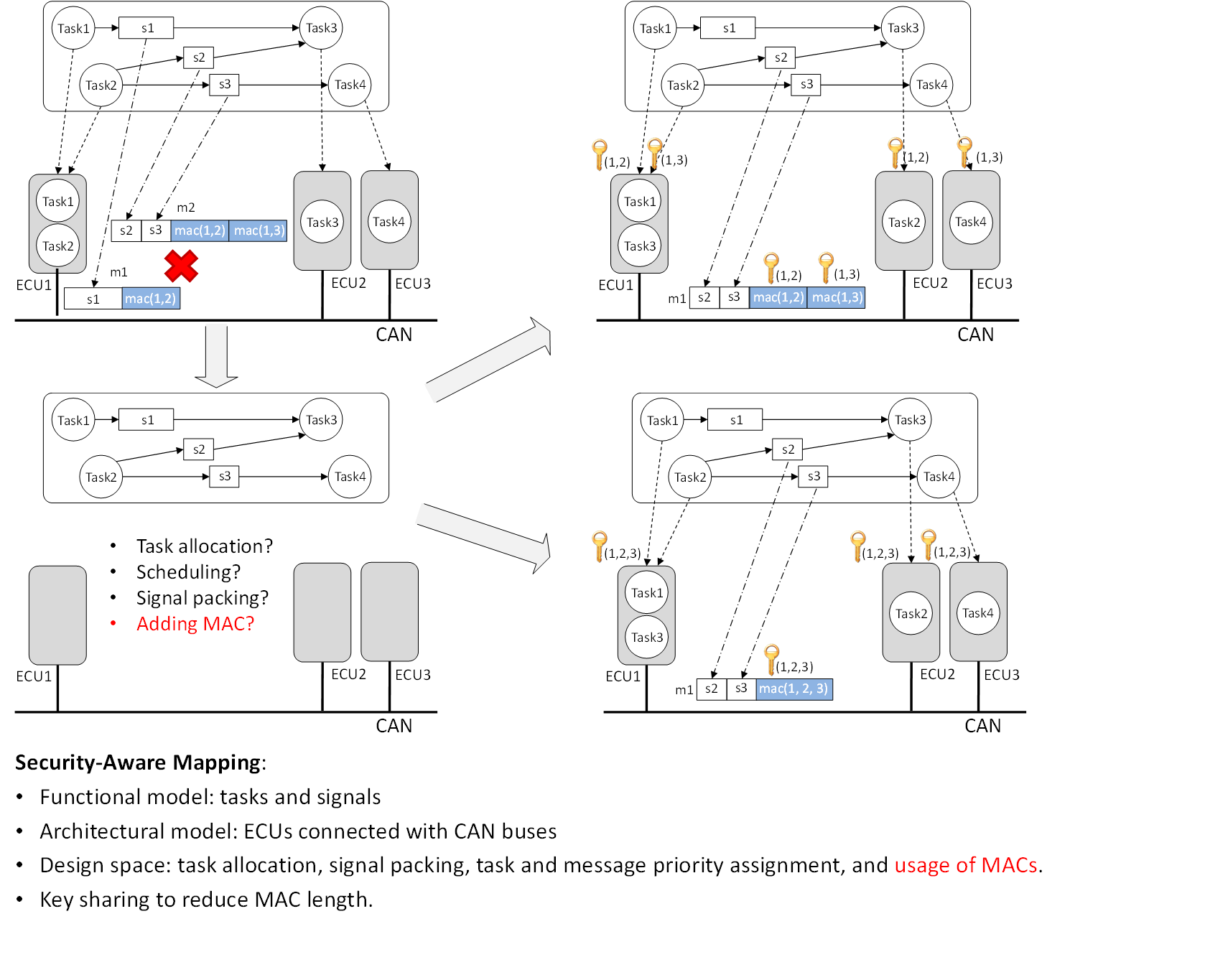
Fig.1 CAN-based system
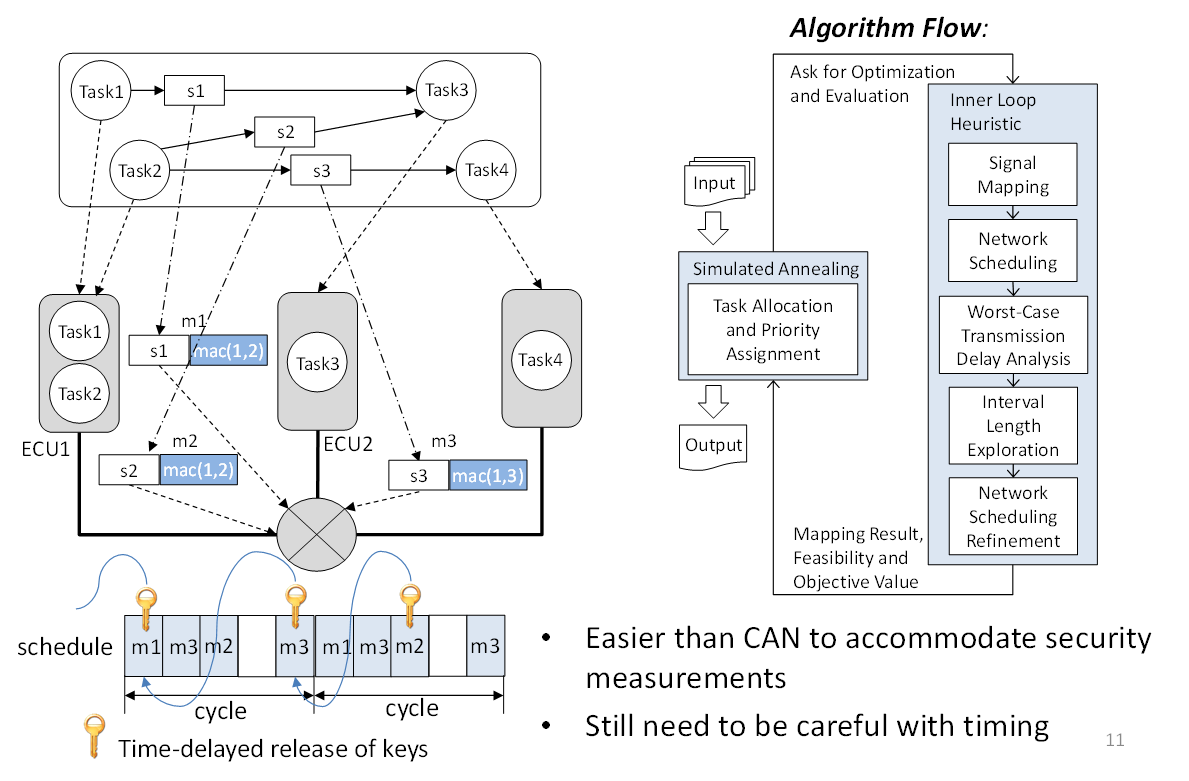
Fig.2 TDMA-based system

Fig.1 CAN-based system

Fig.2 TDMA-based system
Securing the Timing of Cyber-Physical Systems
Overview:
Timing attacks could be particularly destructive for CPS because the correctness of system functionality is affected not only by the data values of operations but also significantly by at what time operations are conducted. We are building a framework for 1) investigating potential timing-based attack surface and strategies, 2) analyzing how timing changes caused by these attacks may affect the overall system properties, and 3) developing control-based and cyber-security defense strategies against timing attacks (including both run-time detectors and design-time mitigation strategies). We focus on vehicle networks and multi-agent robotic systems as main application domains
Framework:
Related Publications: